Introduction
Chapter 1: What is Information Security?
Chapter 2: Indentification and Authentication
Chapter 3: Authorization and Access Control
Chapter 4: Auditing and Accountability
Chapter 5: Cryptography
Chapter 6: Compliance, Laws, and Regulations
Chapter 7: Operations Security
Chapter 8: Human Element Security
Chapter 9: Physical Security
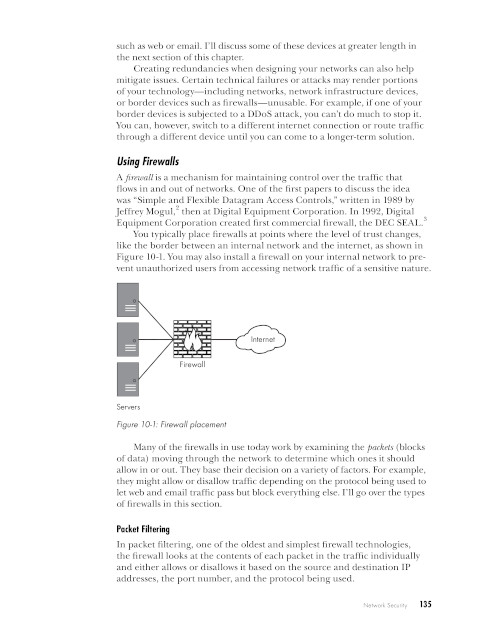
Chapter 10: Network Security
Chapter 11: Operating System Security
Chapter 12: Mobile, Embedded, and Internet of Things Security
Chapter 13: Application Security
Chapter 14: Assessing Security
Notes