Look Inside!
Download Chapter 2: ATTACK TARGETS ON THE INTERNET
How Cybersecurity Really Works is the perfect introduction to cybersecurity. Whether you’re a computer science student or a business professional, it will teach you the basics without all the jargon.
This beginners guide covers different types of attacks, common tactics used by online adversaries, and defensive strategies you can use to protect yourself. You’ll learn what security professionals do, what an attack looks like from a cybercriminal’s viewpoint, and how to implement sophisticated cybersecurity measures on your own devices.
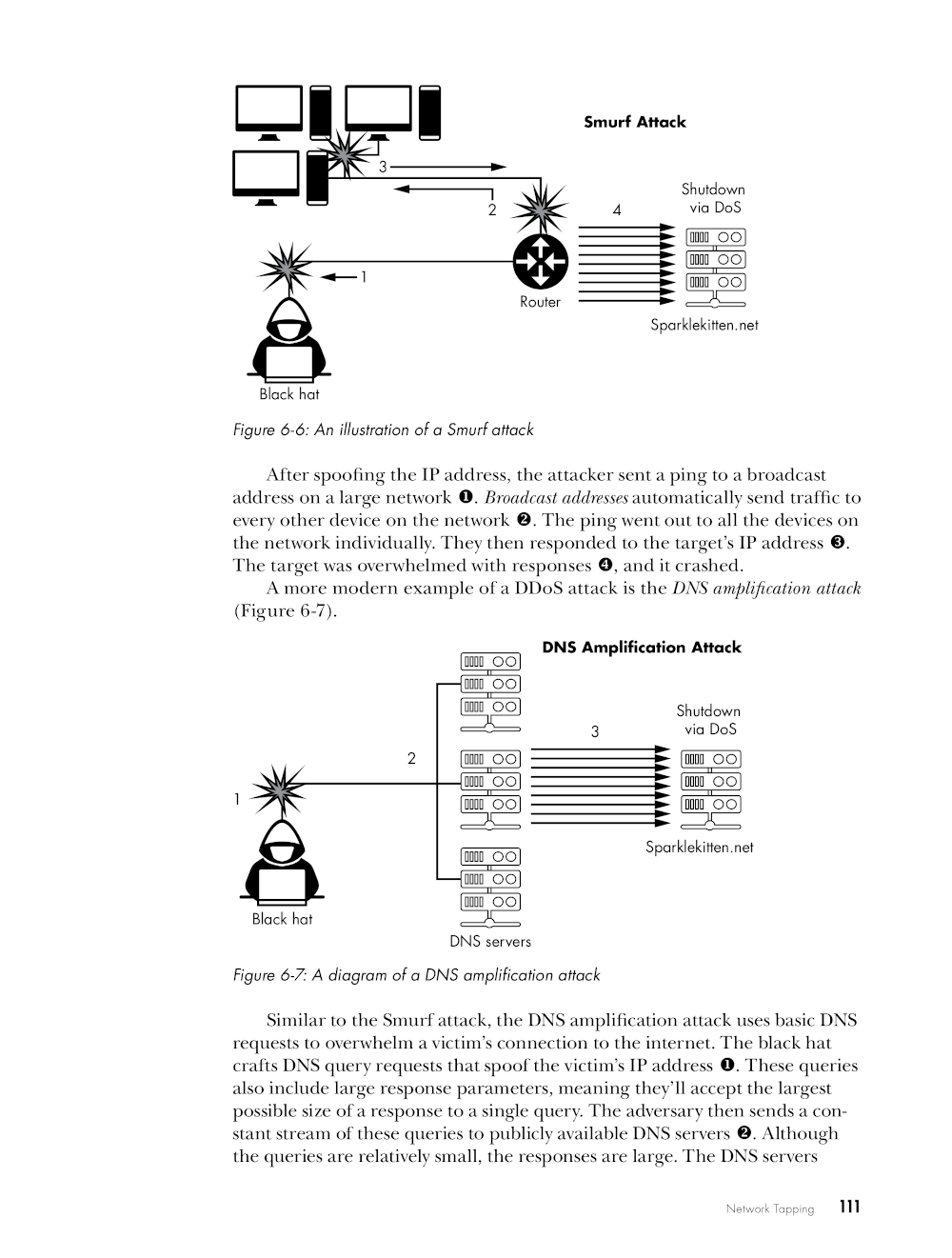
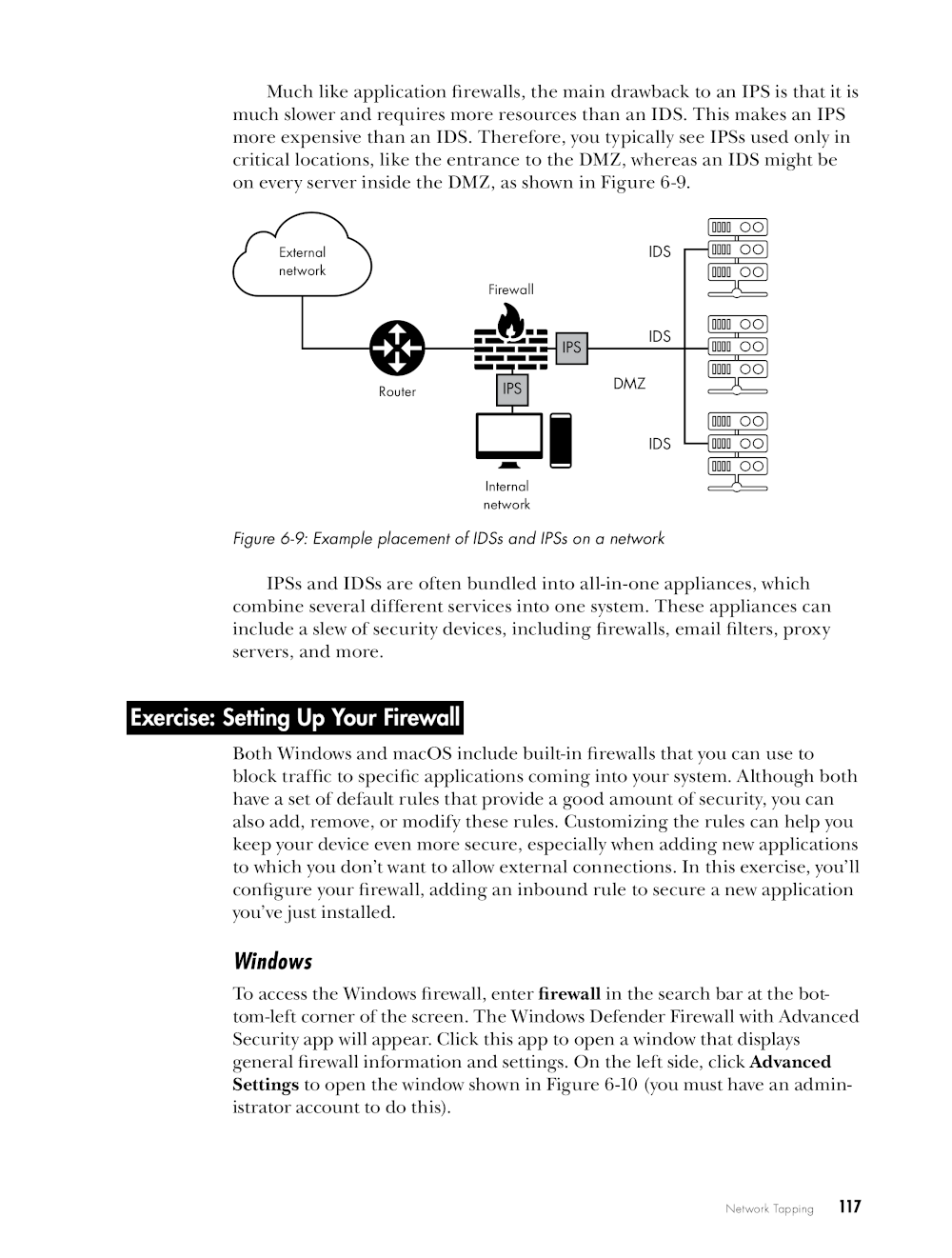
In addition, you’ll find explanations of topics like malware, phishing, and social engineering attacks, coupled with real-world examples and hands-on exercises to help you apply what you’ve learned. You’ll explore ways to bypass access controls, prevent infections from worms and viruses, and protect your cloud accounts from attackers.
You’ll also learn how to:
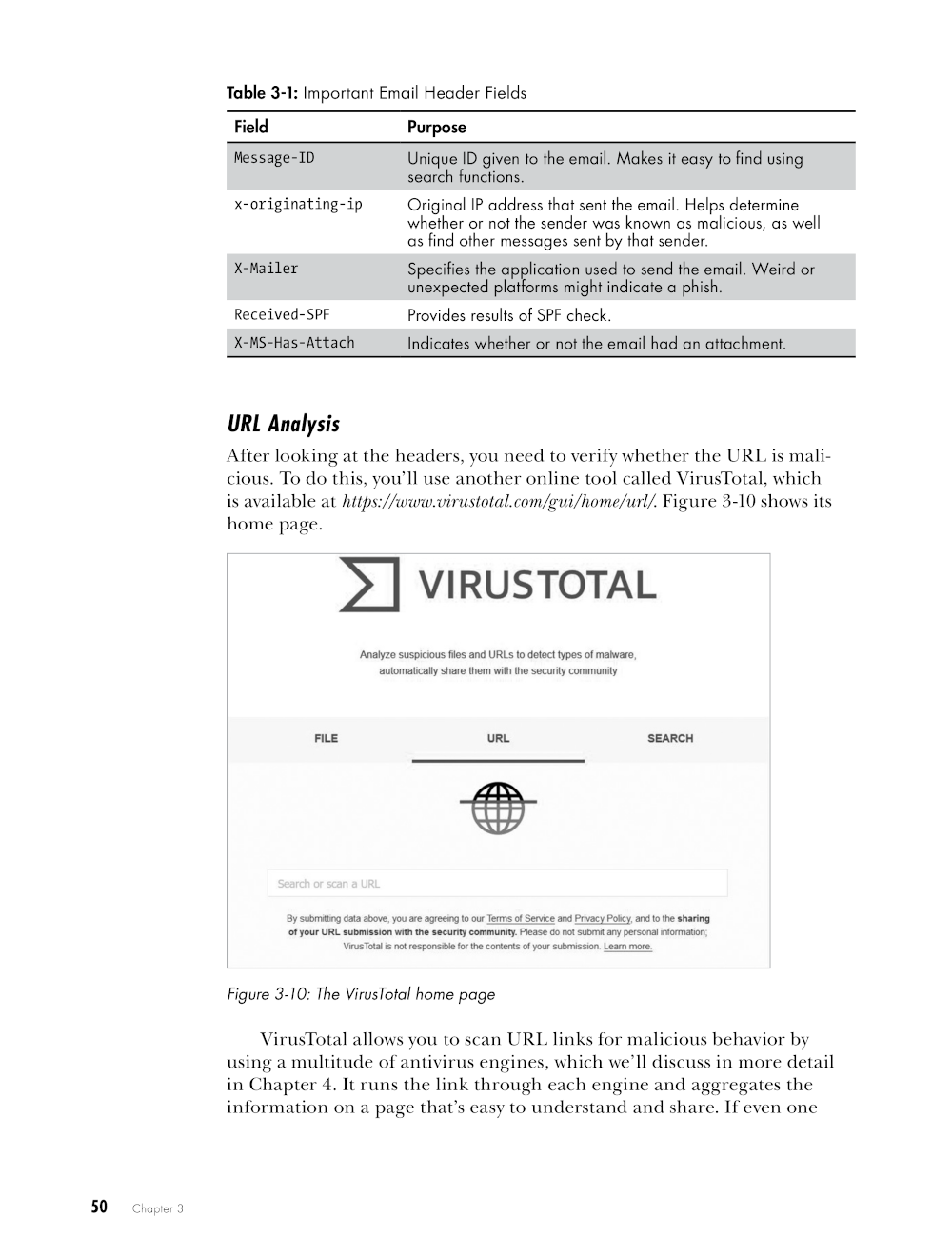
- Analyze emails to detect phishing attempts
- Use SQL injection to attack a website
- Examine malware from the safety of a sandbox environment
- Use the command line to evaluate and improve your computer and network security
- Deploy encryption and hashing to protect your files
- Create a comprehensive risk management plan
You can’t afford to ignore cybersecurity anymore, but attackers won’t wait while you read a long technical manual. That’s why How Cybersecurity Really Works teaches you just the essentials you need to think beyond antivirus and make the right decisions to keep the online monsters at bay.
Download the Chapter 4 maliciouspdf.pdf file on GitHub here. WARNING: The file uses some real exploit code but is rendered completely benign. This allows for more authentic analysis. Still, it may set off Endpoint Security Software and should be used with caution. Download at your own risk.