Introduction
Part I: Vulnerability Management Basics
Chapter 1: Basic Concepts
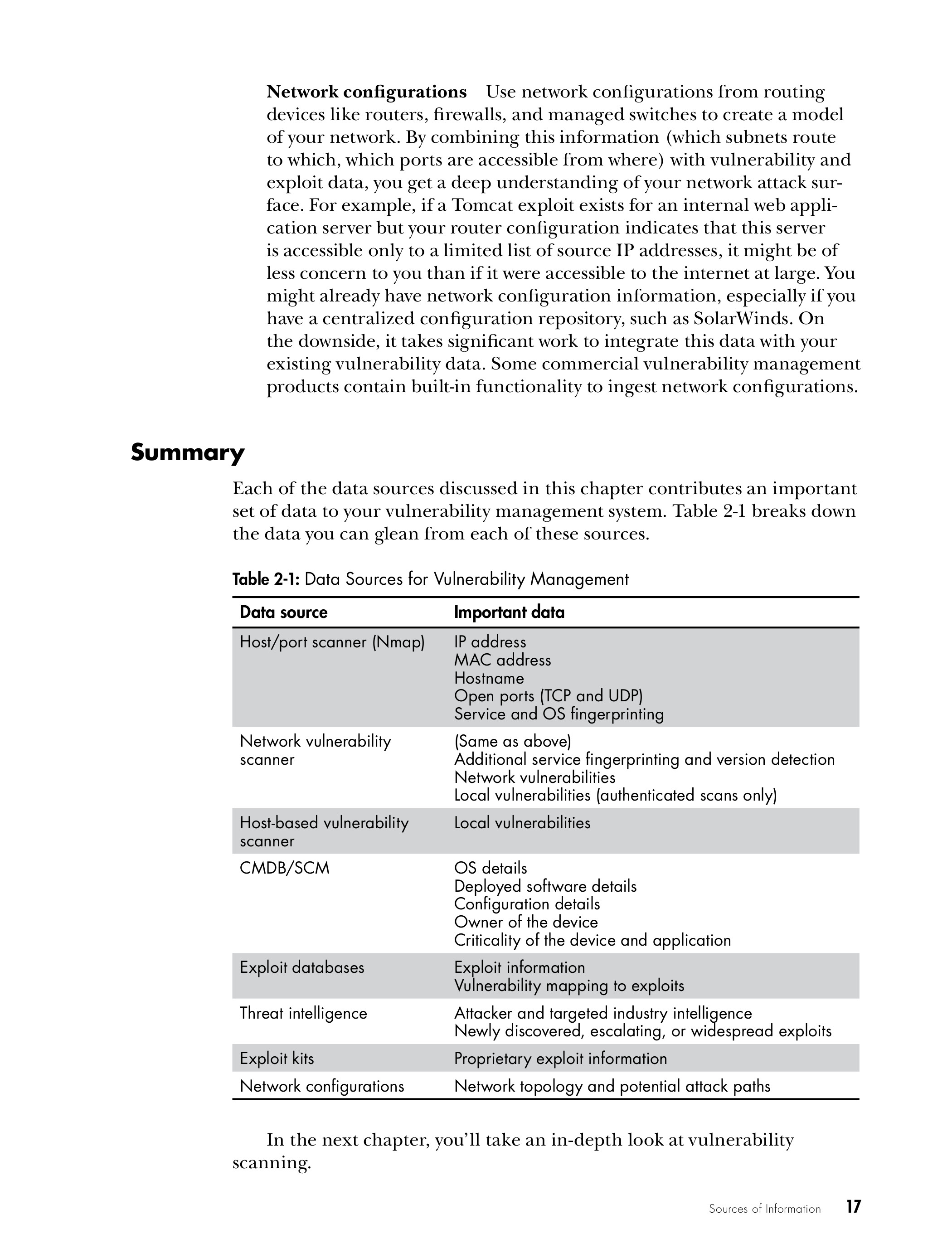
Chapter 2: Sources of Information
Chapter 3: Vulnerability Scanners
Chapter 4: Automating Vulnerability Management
Chapter 5: Vulnerability Management Outcomes
Chapter 6: Vulnerability Management and Organizational Priorities Part II: Hands-On Vulnerability Management
Chapter 7: Setting Up Your Environment
Chapter 8: Using the Data Collection Tools
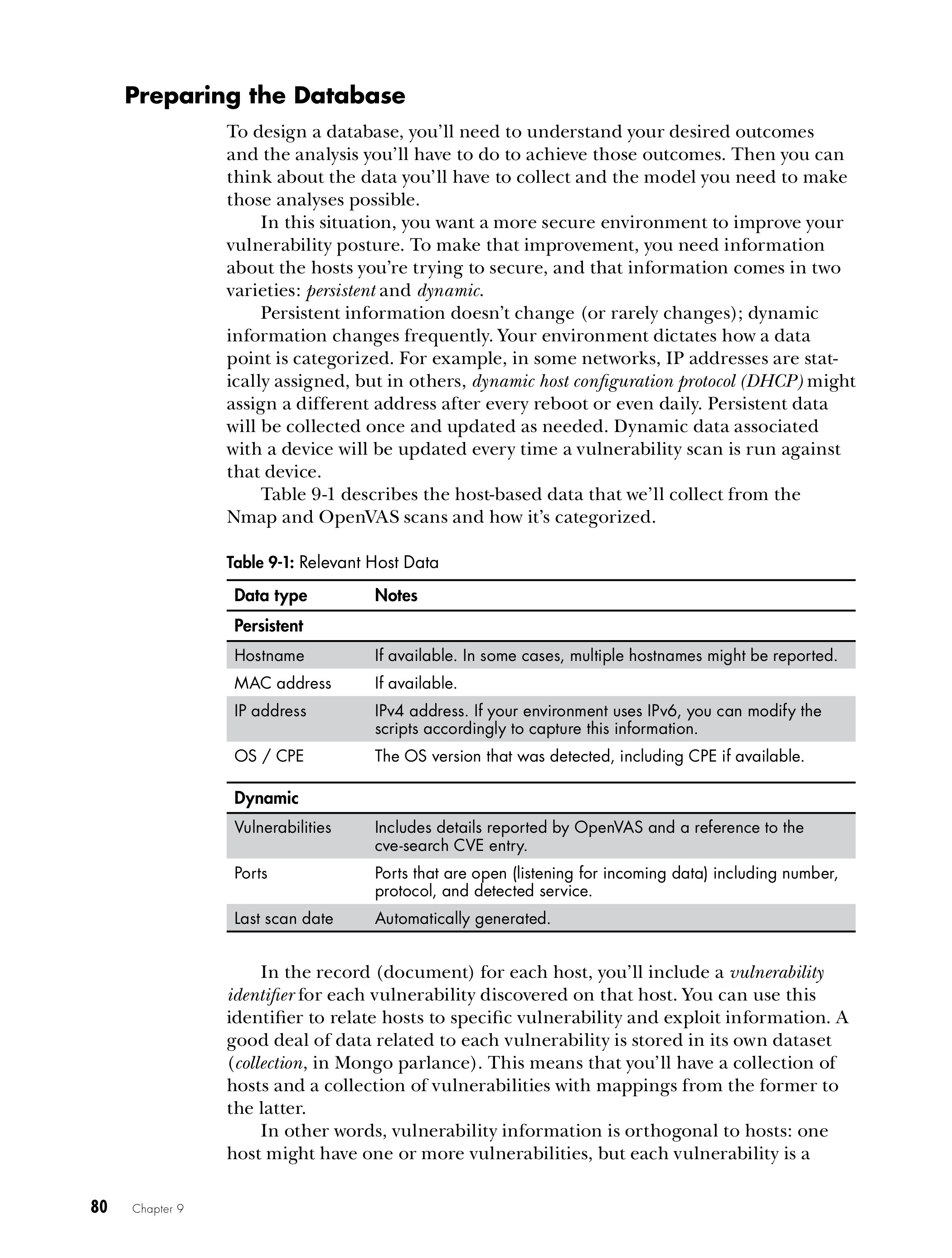
Chapter 9: Getting Your Data Into a Usable Format
Chapter 10: Maintaining the Database
Chapter 11: Generating Asset and Vulnerability Reports
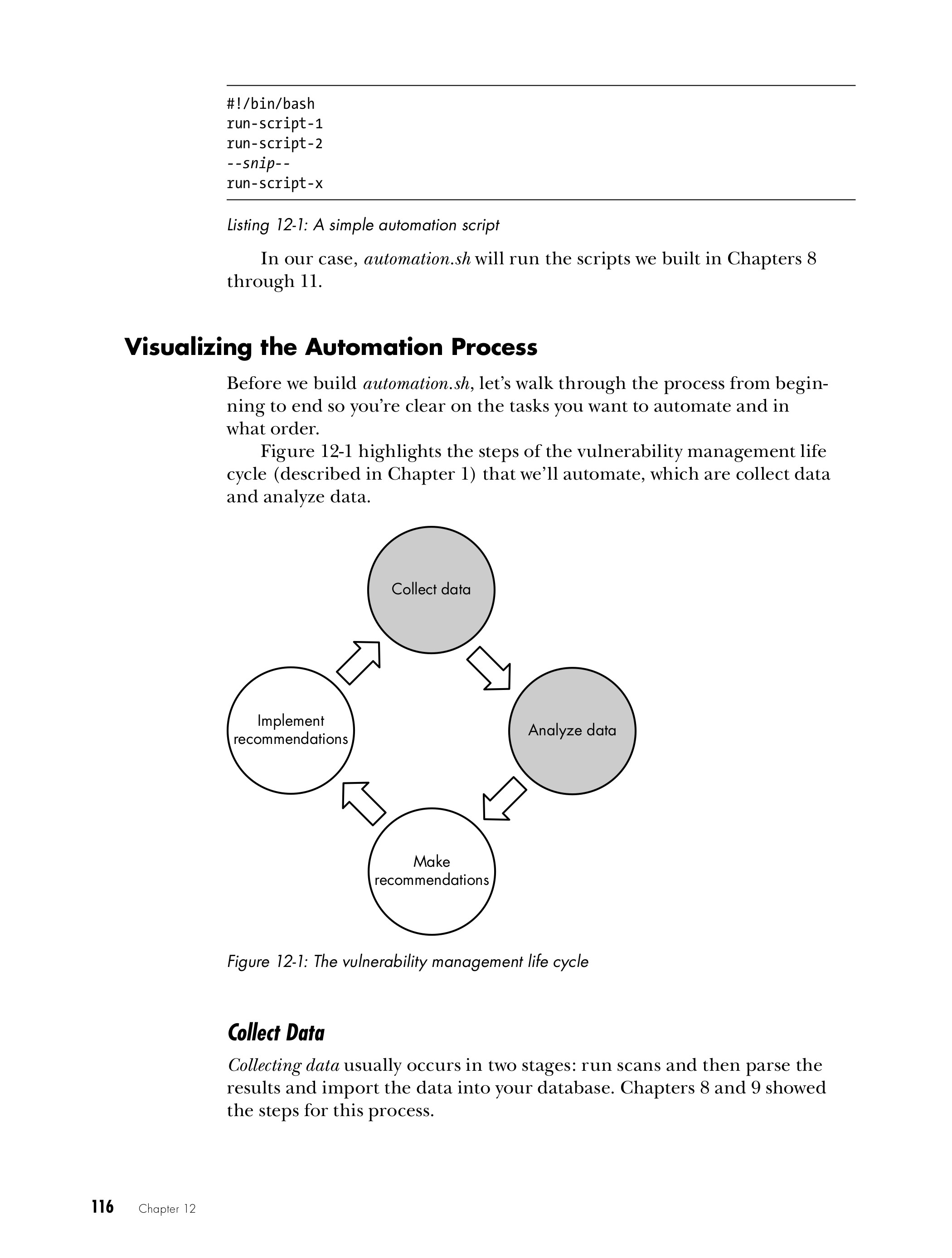
Chapter 12: Automating Scans and Reporting
Chapter 13: Advanced Reporting
Chapter 14: Advanced Topics
Chapter 15: Conclusion
Index
Practical Vulnerability Management
Look Inside!
Download Chapter 2: SOURCES OF INFORMATION
Bugs: they’re everywhere. Software, firmware, hardware — they all have them. Bugs even live in the cloud. And when one of these bugs is leveraged to wreak havoc or steal sensitive information, a company’s prized technology assets suddenly become serious liabilities.
Fortunately, exploitable security weaknesses are entirely preventable; you just have to find them before the bad guys do. Practical Vulnerability Management will help you achieve this goal on a budget, with a proactive process for detecting bugs and squashing the threat they pose.
The book starts by introducing the practice of vulnerability management, its tools and components, and detailing the ways it improves an enterprise’s overall security posture. Then it’s time to get your hands dirty! As the content shifts from conceptual to practical, you’re guided through creating a vulnerability-management system from the ground up, using open-source software.
Along the way, you’ll learn how to:
- Generate accurate and usable vulnerability intelligence
- Scan your networked systems to identify and assess bugs and vulnerabilities
- Prioritize and respond to various security risks
- Automate scans, data analysis, reporting, and other repetitive tasks
- Customize the provided scripts to adapt them to your own needs
Playing whack-a-bug won’t cut it against today’s advanced adversaries. Use this book to set up, maintain, and enhance an effective vulnerability management system, and ensure your organization is always a step ahead of hacks and attacks.
Who is this book for?
Readers should have a basic understanding of coding, but don’t need to be
programmers or security experts to find this book useful.
"An easy read and offers comprehensive solutions to keeping an organization secure and always prepared for possible attacks."
—Helga Labus, Help Net Security
Installing GVM for use with the Practical Vulnerability Management system:
https://github.com/magnua/practicalvm/blob/master/docs/gvm-11.md